Last of all, Permit’s not overlook that this sort of incidents can make the person sense vulnerable and violated and substantially effect their mental well being.
Clone cards are fake versions of actual credit score or debit cards designed by copying the magnetic stripe or chip knowledge from the legitimate card. Fraudsters use card skimmers or hacking techniques to obtain this details, that's then transferred on to a blank card, making it appear much like the authentic.
Once the information is attained, criminals can encode it on to a blank card, developing a precise duplicate of the original. This cloned card can then be utilized to carry out fraudulent transactions or withdraw money within the cardholder's account.
TrustDecision provides personalized techniques that align with the particular needs of various industries. This customization allows reduce Phony positives by concentrating on the most crucial threats relevant to each business enterprise.
Though contactless payment provides a seamless and successful working experience, It is far from solely resistant to cloning makes an attempt. Resourceful criminals have designed specialized equipment effective at intercepting the interaction in between the card and the payment terminal.
The position of EMV microchips in preventing card cloning is very important. Each time a card with an EMV chip is used for a transaction, the chip interacts with the payment terminal to confirm the card’s authenticity.
Nonetheless, card cloning remains a threat, especially in locations or situations where magnetic stripe transactions remain widespread.
Indeed, fraudsters can steal your card information Even though you don’t swipe it. They might use phishing frauds, info breaches, or malware on unsafe websites to capture your info.
Accomplish legitimate hardware independence with an individual golden graphic you'll be able to deploy to any Home windows endpoint, anywhere. With versatile deployments, automatic workflows, in addition to a driver pack library, IT does not get any much easier.
Additionally, consistently monitoring lender statements for almost any unauthorized transactions and immediately reporting any suspicious exercise for the financial institution can support in mitigating the impression of card fraud.
By conducting frequent protection audits and next these actions, businesses can detect and mitigate vulnerabilities, therefore minimizing the risk of card cloning assaults and making certain a secure ecosystem for his or her shoppers.
It’s not foolproof, although. Thieves have designed devices referred to as “shimmers” that operate in A great deal exactly the same way as skimmers, but Focus on cards with EMV chips.
Modern-day robbers have invented methods to reprogram ATMs or POS terminals and get people to share their information and facts this way.
Improved Accuracy: Machine Studying algorithms continually discover from new data, improving upon their potential to tell apart amongst genuine and fraudulent transactions. This minimizes the number of copyright reader Wrong positives and makes certain that authentic transactions will not be unnecessarily flagged.
 Kel Mitchell Then & Now!
Kel Mitchell Then & Now! Spencer Elden Then & Now!
Spencer Elden Then & Now! Angus T. Jones Then & Now!
Angus T. Jones Then & Now!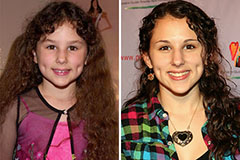 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Mason Reese Then & Now!
Mason Reese Then & Now!